Do you have a web application and still not using SSL? No need to rearchitect your application, you can use a TLS/SSL proxy to front the traffic your application. Among many different choices, Hitch is lightweight, fast, and easy to setup.
If you used Stud in the past, Hitch (website: hitch-tls.org) is the modern version of it. Hitch is being actively developed by Varnish Software. You might be already familiar with Varnish, a very popular open-source caching proxy.
Since it is a fairly recent revival, usually there is not a lot of prebuilt packages available. Fortunately, Hitch is a rather small project, just a couple of C source files. Building it from source takes only a few minutes.
First, make sure you have the necessary tools.
With a recent Debian or Ubuntu system, it is a matter of installing a few packages:
sudo apt-get install -y pkg-config build-essential libev-dev libssl-dev
If you are on macOS, install the equivalent packages to libev and OpenSSL. Since I’m using Nix (because it’s a wonderful package manager), I also need to set a couple of environment variables so that those packages will be properly discovered:
nix-env -i libev openssl
export LIBEV_DIR=$(nix-env -q --xml --out-path libev| grep -Eo "\"(/nix.+)\"")
export LIBSSL_DIR=$(nix-env -q --xml --out-path openssl| grep dev| grep -Eo "\"(/nix.+)\"")
export SSL_CFLAGS="-I $LIBSSL_DIR/include -L $LIBSSL_DIR/lib"
export SSL_LIBS=-lssl
export CRYPTO_CFLAGS="-I $LIBSSL_DIR/include -L $LIBSSL_DIR/lib"
export CRYPTO_LIBS=-lcrypto
export CFLAGS="-I $LIBEV_DIR/include -L $LIBEV_DIR/lib $SSL_CFLAGS"
Let’s download the source tarball and compile the code:
curl https://hitch-tls.org/source/hitch-1.2.0.tar.gz -O
openssl md5 hitch-1.2.0.tar.gz | grep "f2f19b6e92115c083d0fccf59b7bd856"
tar zxf hitch-1.2.0.tar.gz
cd hitch-1.2.0
./configure --with-rst2man=/bin/true
make
Check the executable to ensure that everything is built properly:
$ src/hitch --version
hitch 1.2.0
You can also verify that Hitch does not have a lot of dependencies (shown here on Ubuntu 14.04):
$ ldd src/hitch
linux-vdso.so.1 => (0x00007ffd393e0000)
libssl.so.1.0.0 => /lib/x86_64-linux-gnu/libssl.so.1.0.0 (0x00007f39587fb000)
libcrypto.so.1.0.0 => /lib/x86_64-linux-gnu/libcrypto.so.1.0.0 (0x00007f395841f000)
libev.so.4 => /usr/lib/x86_64-linux-gnu/libev.so.4 (0x00007f3958210000)
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f3957e4b000)
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007f3957c47000)
libm.so.6 => /lib/x86_64-linux-gnu/libm.so.6 (0x00007f3957940000)
/lib64/ld-linux-x86-64.so.2 (0x00005600f800e000)
For a quick sanity check, we can create a test certificate:
sudo apt-get install -y ssl-cert
sudo make-ssl-cert /usr/share/ssl-cert/ssleay.cnf example.pem
sudo chmod +r example.pem
Now assuming there is an HTTP server running on port 8000, Hitch can be invoked as follows:
src/hitch --frontend=[*]:8443 --backend=[localhost]:8000 example.pem
Open your favorite web browser and go to that URL on port 8443 (the browser might give a warning first, due to our test certificate). Hitch will receive that request, handle TLS, and pass the unencrypted connection to the backend running on port 8080:
[ 7435] 10.0.2.2:62635 :0 8:9 proxy connect
[ 7435] 10.0.2.2:62635 :0 8:9 ssl handshake start
[ 7435] 10.0.2.2:62635 :0 8:9 ssl client handshake revents=1
[ 7435] 10.0.2.2:62635 :0 8:9 ssl client handshake err=2
[ 7435] 10.0.2.2:62635 :0 8:9 ssl client handshake revents=1
[ 7435] 10.0.2.2:62635 :0 8:9 ssl end handshake
[ 7435] 10.0.2.2:62635 :60641 8:9 backend connected
[ 7435] 10.0.2.2:62635 :60641 8:9 Connection closed by backend
[ 7435] 10.0.2.2:62635 :60641 8:9 proxy shutdown req=1
[ 7435] 10.0.2.2:62635 :60641 8:9 proxy shutdown req=0
Obviously, I recommend that you configure Hitch properly (choosing a set of suitable ciphers, etc) depending on your need. Meanwhile, running CipherScan on the default settings will get you:
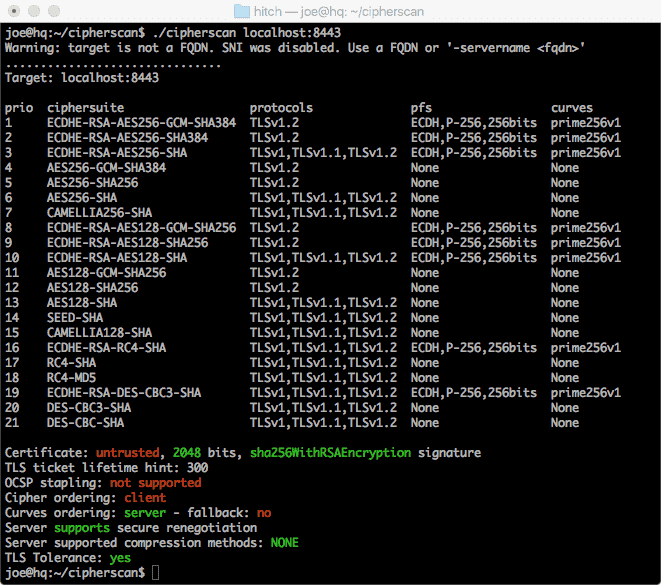
Hitch is not the only approach to terminate TLS/SSL. Yet, if you are still looking for a solution, give it a try and you have no more excuse not to enable HTTPS for everything!