If you are running an HTTP server and would like to enable SSL, an easy way to do that is to use a terminating proxy. Among others, stunnel is relatively simple and very easy to use.

Many Linux distributions, including Debian and Ubuntu, already made stunnel package available. Thus, installing it is as straightforward as:
sudo apt-get install stunnel4
To verify the installation:
$ stunnel -version
stunnel 5.30 on x86_64-pc-linux-gnu platform
Compiled with OpenSSL 1.0.2e 3 Dec 2015
Running with OpenSSL 1.0.2g 1 Mar 2016
Note that stunnel is very capable, it can do more than just upgrading a web server from HTTP to HTTPS. For this blog post however, that will be the only thing we will cover.
For testing purposes, it is sufficient to use a test certificate:
sudo apt-get install -y ssl-cert
make-ssl-cert /usr/share/ssl-cert/ssleay.cnf example.pem
sudo chmod +r example.pem
Various examples of configuration are available. For this use case, we could create a simple configuration containing the following lines (note that the pid needs to be an absolute path):
pid = /home/ariya/stunnel.pid
[https]
accept = 8443
connect = 8080
cert = example.pem
If we name it webserver.conf, then stunnel can be activated with it by running:
stunnel webserver.conf
Assuming there is a web server running on port 8080, the HTTPS version will be made available by stunnel on port 8443. To check that, simply open your favorite web browser and point it to localhost:8443. Typically there will be a warning due to the above self-sign test certificate, but otherwise it should work just fine.
Running CipherScan tool from Mozilla on the default stunnel configuration gives the following:
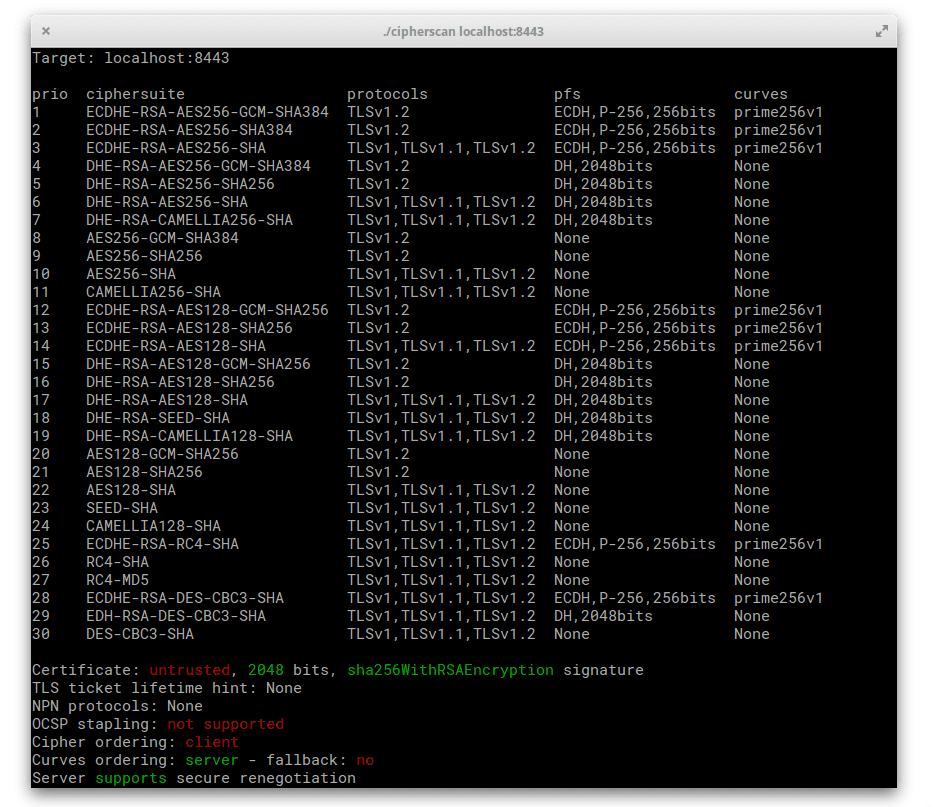
Of course, it is highly recommend to tweak the ciphers based on your requirements. Do not forget to refer to its excellent documentation.
Now, you have less excuse not to enable HTTPS for everything!